Finalizing Malware Analysis Environment
So earlier this week, I went over the creation of my malware analysis lab. Today I will finish setting it up
Part VI: Installing Openvm-tools
Following these directions, I was able to successfully install OpenVM Tools within my FreeBSD environment. It took a couple reboots, but everything worked as expected. It was nice to finally have something work on the first couple tries!
Part VII: Installing Xen Orchestra
This one was pretty easy. Xen Orchestra requires 4GBs of RAM, and a few dependencies specific to FreeBSD. These are:
• gmake
• redis
• python
• git
• npm
• node
• autoconf
• gifsicle
• jpeg-turbo
• optipng
• yarn
• npm
• node
Easily enough, all of these packages can be installed with:
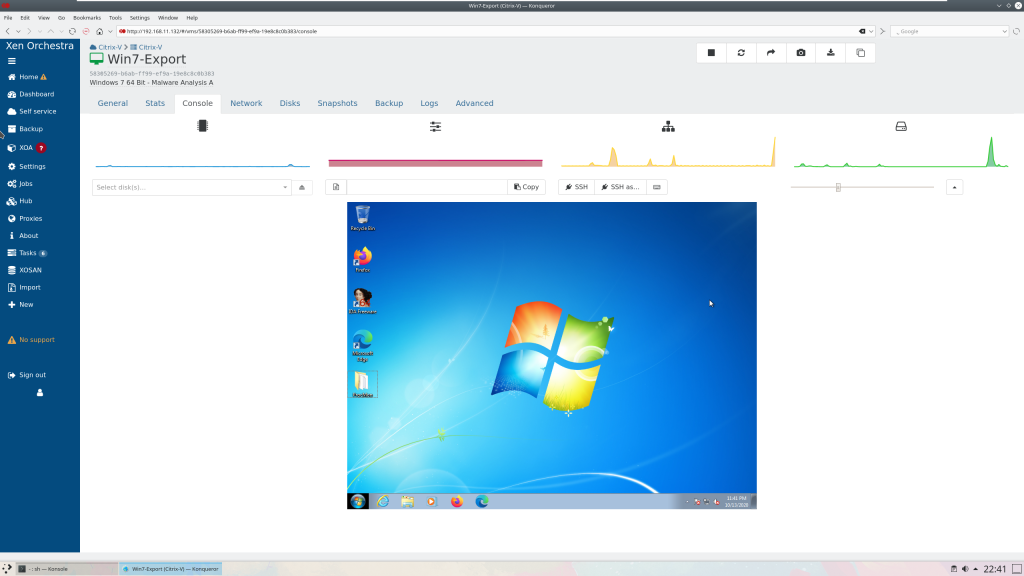
pkg install gmake redis python git npm node autoconf jpeg-turbo optipng gifsicle npm nodeAfter everything is installed, you can then follow the official documentation. Once built, configured, logged in, and attached to your XenServer, it will look like this:
Part VIII: Implement Firewall Rules
Out of everything in the lab, this is the absolute most important. Without adequate firewall rules, the Windows 7 VM can interact with anything on the network. This is… not good. Especially considering most malware nowadays can spread at the speed of light. So, we will need to implement rules in order to protect everything on the network. Currently, my router acts as my firewall, so we will configure it from there.
The first part is to connect the XenServer to an open port, and assign a new VLAN to it. For my setup, the server is connected to port 3 and I have assigned it VLAN 12:
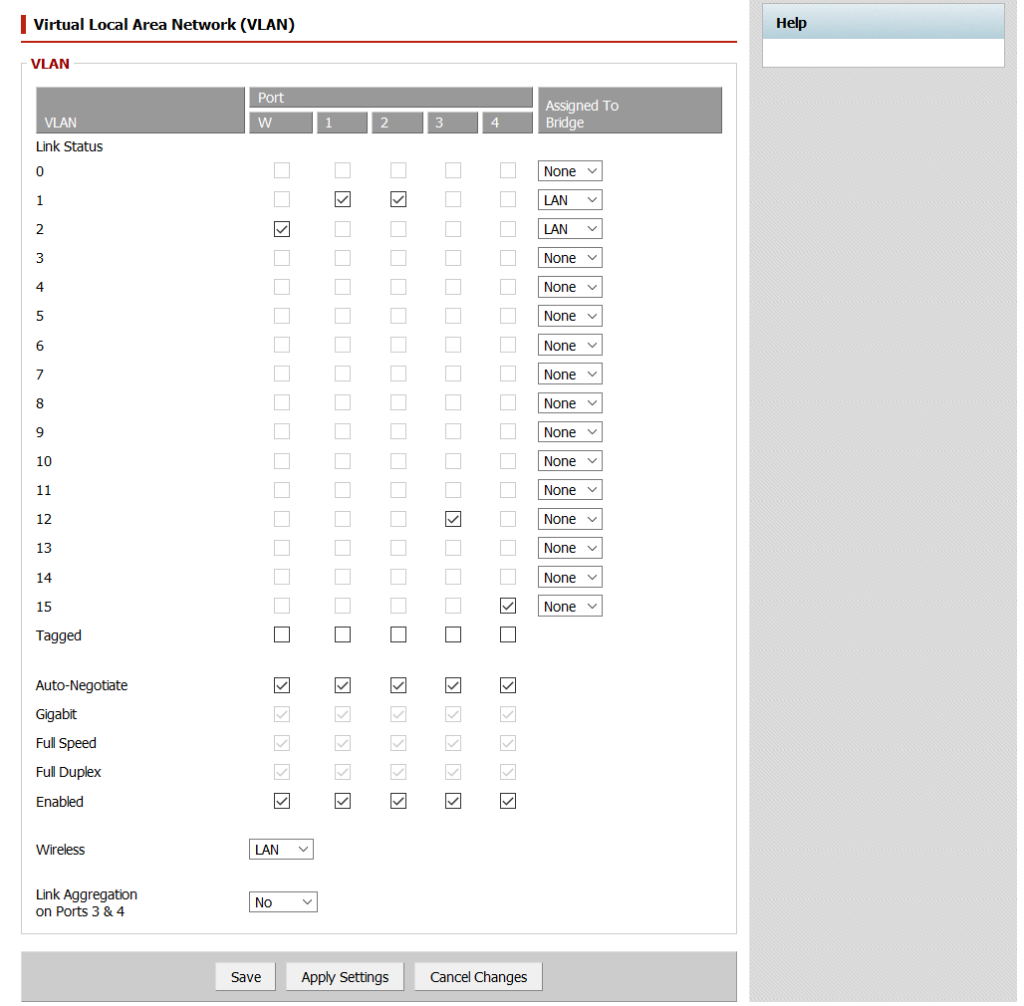
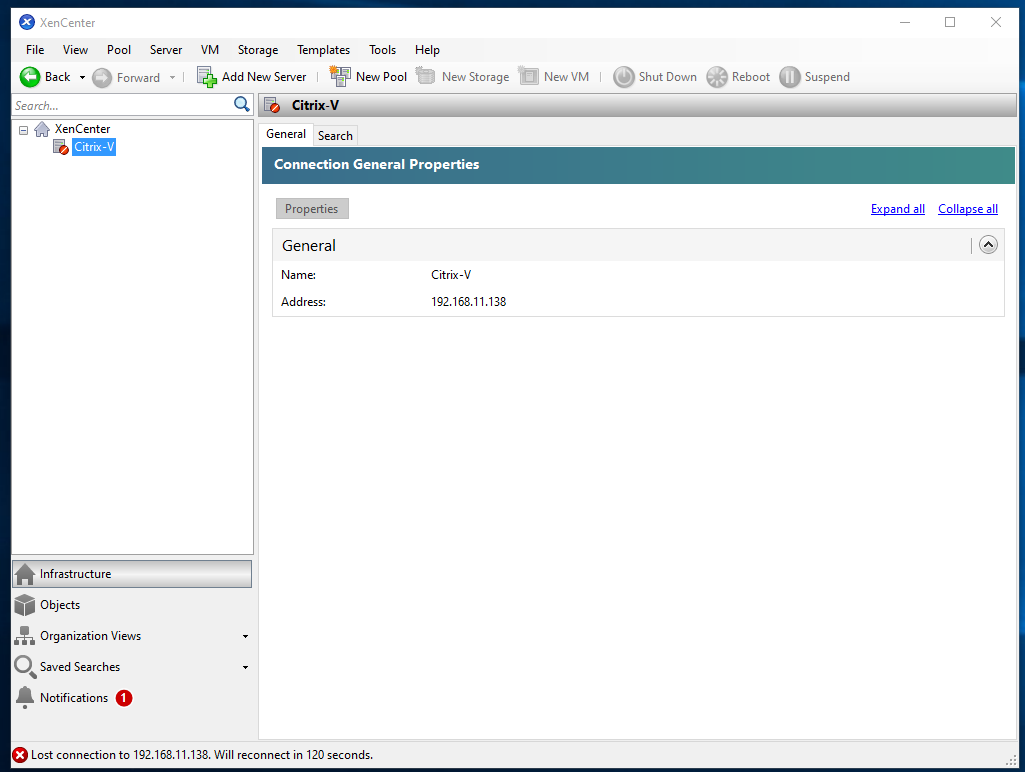
This will reboot the router, and once the router comes back up, port 3 no longer has access to the network. We can identify this from our previously connected XenCenter reports the XenServer offline:
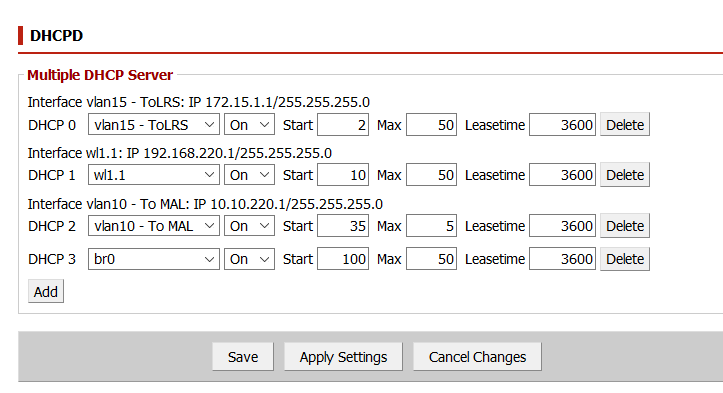
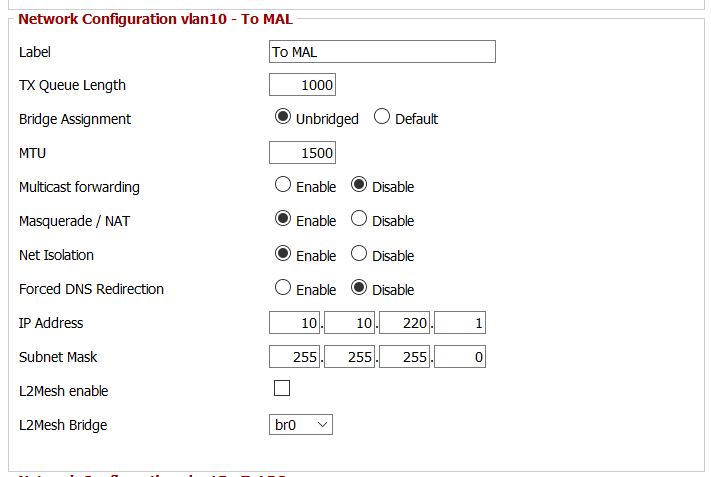
Now its time to configure our VLAN. I labeled it “To MAL”, enabled NAT masquerade, net isolation, and assigned an IP address of 10.10.220.1. The DHCP server is set to start at .35 and have a maximum of 5 IPs:
Finally, I have to write the firewall rules, which will have to come later. Until next time!